Project Details
We aim to introduce quantum-resistant algorithms to commonly used communication protocols. Our goal is to provide secure and practical solutions for relevant Virtual Private Networks (VPNs).
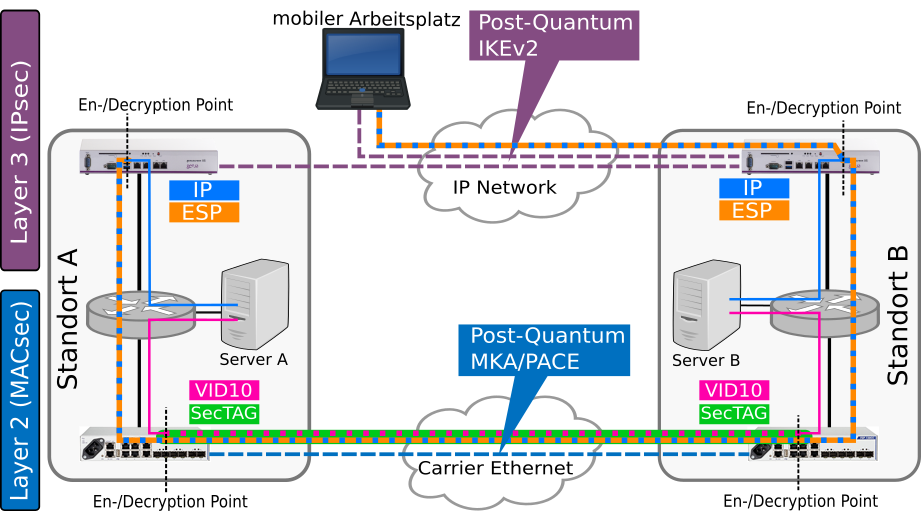
Several communication protocols describe secure links on different layers of the OSI model (link to Wikipedia). Many protocols differ between the actual communication channel and (different) key exchange or key agreement protocols. While in most cases the first are relatively easy hardened against quantum computer based attacks, the latter depend on the exchange of the currently used cryptographic schemes. Depending on the protocol this can be a challenging task.
IPsec and IKEv2
IPsec is a popular suite for communication. One of the main use cases is the establishment of secure communication channels e.g. between different company sites over IP networks / the Internet. The most commonly used key exchange protocol in the context of IPsec is the Internet Key Exchange Version 2 (IKEv2) which is based on a Diffie-Hellman key exchange. This one has to be exchanged or supplemented by other (quantum-resistant) schemes. Issues like a limitation in total key size and (other) peculiarities coming from fragmentation require a reasoned integration and handling of new schemes.
MACsec and MKA/PACE
The IEEE standard 802.1AE - commonly known as MACsec - describes secure communication on OSI layer 2. Key exchange is realized by using protocols like MKA or PACE. In this project we focus on fiber switches connecting different locations providing secure communication for several (authenticated) users.
Hybrid solutions and crypto agility
There is a downside to new cryptographic schemes. While experts scrutinize new algorithms and the use of the latter happens to the best of the knowledge of the crypto community, confidence in new schemes can only build slowly. It is always possible that advances in cryptanalysis, super computing or implementation errors cause security issues. This holds for new quantum-resistant schemes just as well as for classical ones. Therefore it is sensible to use several cryptographic schemes in parallel, e.g. deviating a shared secret from several key exchanges using different crypto primitives. To offer such a solution, modular designs of the used protocols are inevitable. In the end this leads to crypto agility. This projects has an eye on solutions where algorithms may be exchanged as easily as possible (if possible) or combined with other schemes.
Multi-layer security
Secure data transfer is facilitated in different ways. An end user wishes for end-to-end security. This can only be accomplished if an applicataion e.g. encrypts data which is only decrypted at the destination end-point. As providers and carriers cannot assume that each user of their infrastructure is taking care of securing the communication, it is only reasonable to take care of data integrity, secrecy and authentication at each possible step. This can lead to quite an overhead on data transfer. In this project we take a look at using quantum-safe (hybrid) solutions on different layers in parallel and the resulting effects.